Seclore for Microsoft Sensitivity Labels
With Seclore for Microsoft sensitivity labels you can use Microsoft sensitivity labels to protect Office 365 documents with Seclore. Simply configure sensitivity labels with Seclore’s protection policies and protect documents by selecting the configured labels.
As soon as you select a sensitivity label that’s mapped to Seclore’s protection policies and close the document, it gets protected.
In this section, we'll see how to configure Seclore for Microsoft Sensitivity Labels in Seclore after you've configured it in the Microsoft Azure portal.
Click Add Component to start configuring Seclore Microsoft Sensitivity Labels.
Let's go through component details along with each parameter and its value.
Component details
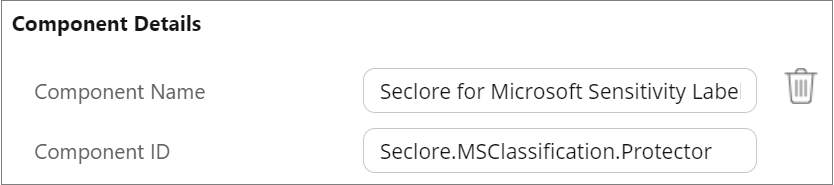
- Component Name: Seclore Microsoft Sensitivity Labels
- Component ID: Seclore.MSClassification.Protector
Click Add Parameter to add the following parameters.
App name
Add this parameter to enter the application name you entered while registering Seclore for Microsoft Sensitivity Labels in the Microsoft Azure portal.
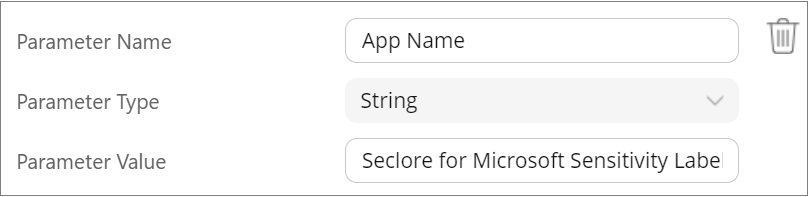
- Parameter Name: App Name
- Parameter Type: String
- Parameter Value: Enter the application name you entered while registering Seclore for Microsoft Sensitivity Labels in the Microsoft Azure portal.
Client ID
Add this parameter to enter application/client ID generated in the Microsoft Azure portal after you registered Seclore for Microsoft Sensitivity Labels.
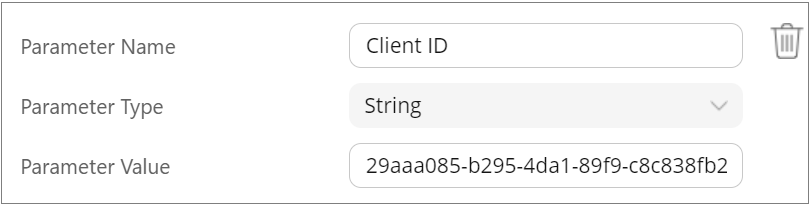
- Parameter Name: Client ID
- Parameter Type: String
- Parameter Value: Enter the application/client ID generated in the Microsoft Azure portal after you registered Seclore for Microsoft Sensitivity Labels.
Tenant ID
Add this parameter to enter the tenant ID generated in the Microsoft Azure portal after you registered Seclore for Microsoft Sensitivity Labels.
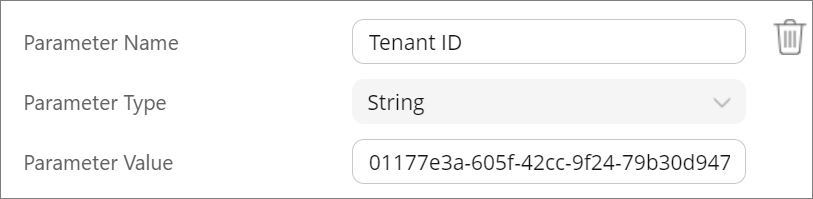
- Parameter Name: Tenant ID
- Parameter Type: String
- Parameter Value: Enter the Tenant ID generated in the Microsoft Azure portal after you registered Seclore for Microsoft Sensitivity Labels.
App version
Add this parameter to enter the app version of Seclore for Microsoft Sensitivity Labels.
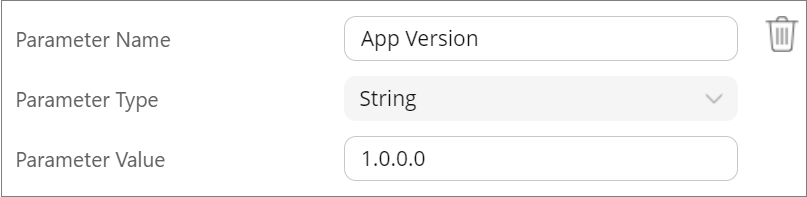
- Parameter Name: App Version
- Parameter Type: String
- Parameter Value: Enter the version of Seclore for Microsoft Sensitivity Labels you wish to configure. The current version is 1.0.0.0.
Policy mapping
Add this parameter to map Seclore policies with the labels configured in the Microsoft Azure portal.
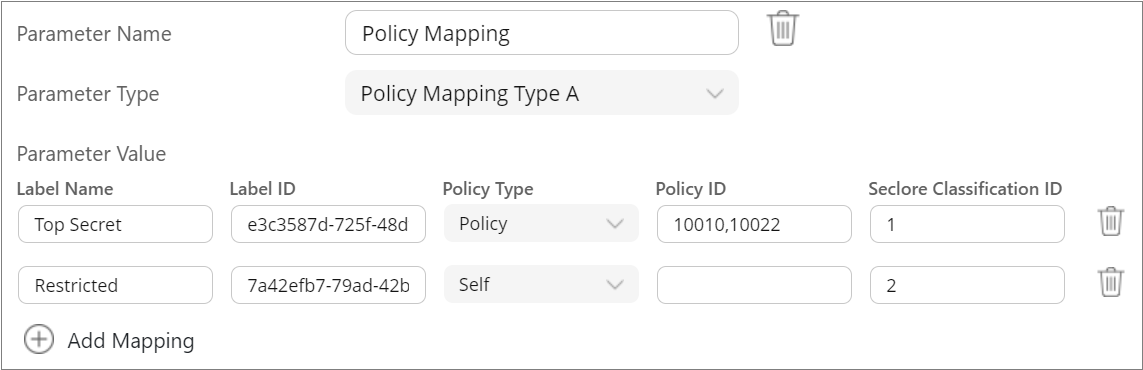
- Parameter Name: Policy Mapping
- Parameter Type: Policy Mapping Type A
- Parameter Value: Here, you'll add labels and map them to Seclore policies. Click Add mapping to start mapping labels.
![]()
You need to add a row for each label. Enter the following details in each row of label mapping.
- Label Name: Enter the sensitivity label defined in Microsoft Azure portal.
- Label ID: Enter the label ID generated in Microsoft Azure portal. Label ID can be found in Microsoft 365 compliance center > More resources > Open in Azure information Protection > Labels > Click on the label. The label ID is seen at the bottom of the page. Here's an example of a label ID: 790f8f7e-e0bf-4c0a-836c-6f1ce91f6734
- Policy Type: Enter Policy if you wish to map the label with predefined policy(ies) you've created in Seclore. When users select a label for a file or email, it'll get automatically protected with the policy ID(s) you enter in the next column.
- Enter Self if you want files to get protected with default permissions.
- Policy ID: If you entered Policy in the previous column, enter the policy ID(s) here. When users select a label for a file or email, it'll get automatically protected with the policy ID(s) you enter here. You can also enter multiple policy IDs separated by commas. For example, 1001, 1002, 1003, etc.
- Seclore Classification ID: Enter the classification ID of the Seclore Classification label that you wish to map to this sensitivity label. Your Global Security Admin can see the classification ID under Policies > Classification Policies > Labels > *Label Name* in your Policy Server portal.
Click Save when you're done. The changes may take up to 24 hours to be applied.